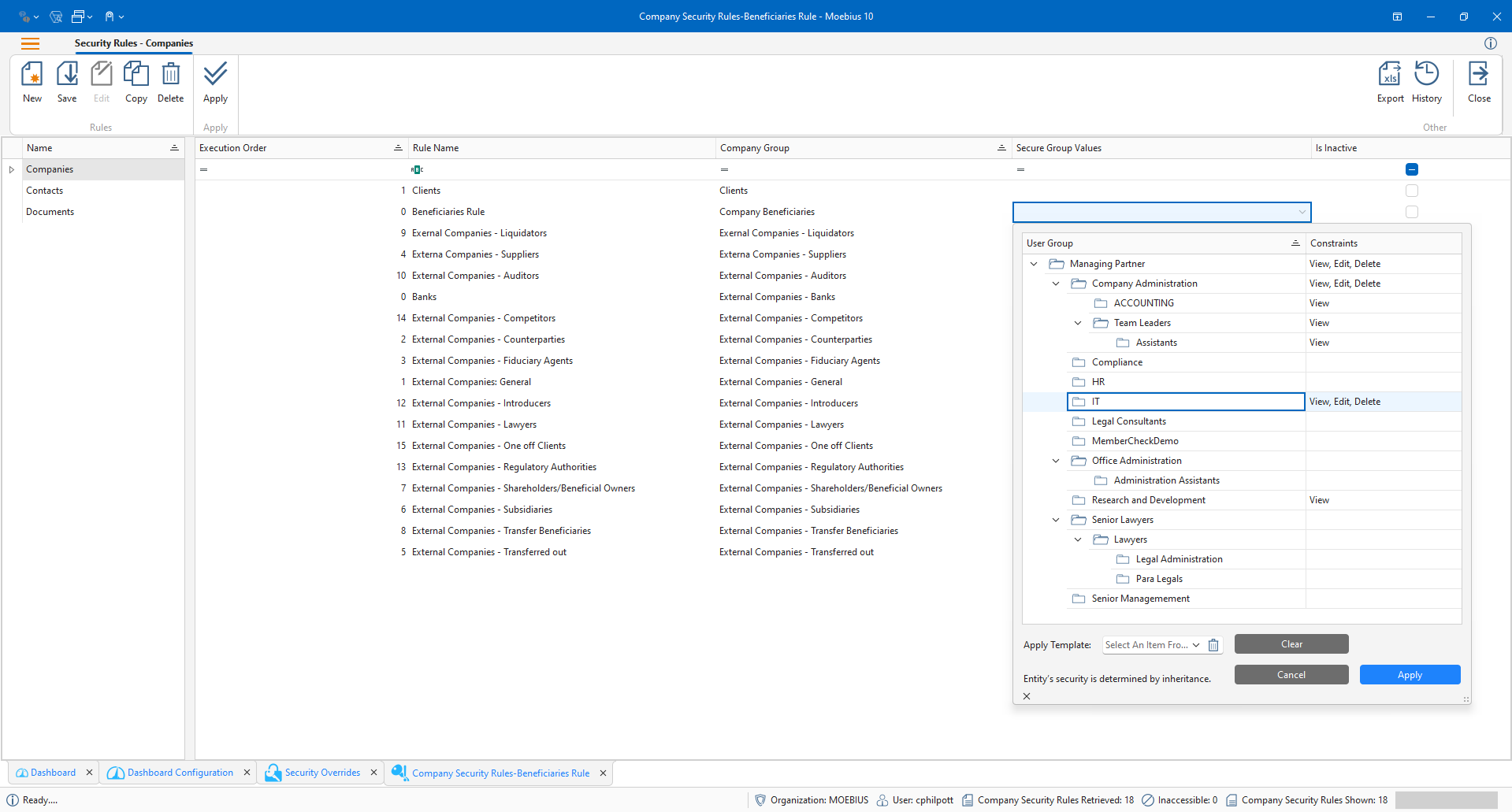

Our system of fully customizable and precise user access combined with 2FA, and end-to-end encryption protects your data and documents against unauthorized access and data leakage.

Regular penetration testing helps us to proactively identify and fix vulnerabilities, ensuring that the possibility of unauthorized access and security threats are minimised.

Use powerful and flexible security tools to organize your personnel into workgroups with tailored access and keep full control over access to your data, documents and system modules.